
[ad_1]
Detecting that your Mac has been hacked is a complicated task, mainly because one of the goals of hackers is for their activity to go unnoticed. However, there are more or less suspicious symptoms such as remote access, sudden slowness, applications that you have not installed, redirects… if you suspect that your Apple computer has been hacked, here you go a list of recommendations to stop or prevent further damage to your Mac. Of course, in any case it will depend on the type of attack and access.
Disconnect your device from the internet and turn off Bluetooth
The Internet is the great way to access your Macwhether with remote desktop protocols (RDP), SSH and Man-in-the-Middle (MITM) attacks on unsecured networks or using malware to collect your data.
When we talk about unsecured networks, they are usually public or easily accessible Wi-Fi, for example in an airport or a cafeteria. So if you suspect that the attack is coming from here, the first thing you should do is turn off your Wi-Fi and Bluetooth from system preferences as soon as possible.
This disconnection is a temporary measure so that, while you are offline, you can try to discover the origin of the attack and take measures to avoid it.

Change passwords and access credentials
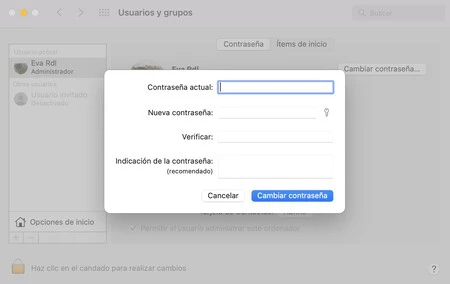
The first thing you should do when you suspect that an intruder can access your Mac is to increase security by changing passwords. And if you don’t have a password to enter the computer, it’s time to activate it. In any case, make sure that the new passwords are robust and difficult to deduce.
Among the passwords you should change:
- Your administrator account and other usersfrom ‘System Preferences’ > ‘Users and Groups’.
- The password of Wi-Fi and access from your router.
- Your Apple ID passwordessential to access the most sensitive information on your devices and iCloud.
- Email and account passwordsfor example from your Gmail account, social networks, banking entities, places where you shop online.
These operations will take a while, but they will prevent unauthorized access and protect important personal information for you. But how to do it if we have disconnected our Mac from the internet? From another device you trust.
Activate isolation mode
macOS has an emergency mode that you can activate in case you suspect intruders on your computer: it’s called ‘Isolation mode‘ (available starting with macOS Ventura, if you have an older OS you won’t find it) and you can find it in ‘System Preferences’ > ‘Security & Privacy’.
Between the measures that execute this hermetic mode found: disable message attachments, links, and link previews, cut off FaceTime calls and invitations from people not in your contacts list, disable shared albums, and stop some web browsing features. The objective is to be able to have connectivity to take advantage of it, but take extreme precautions.
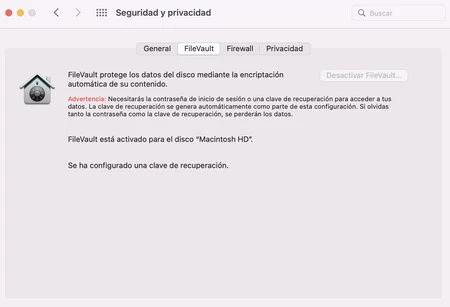
Better with FireVault
One of the best features available in the ‘Security and Privacy’ section is ‘FireVault’, a built-in encryption system that protects your storage drive and the data it houses.
It works automatically when you turn on the device, encrypting the information and decrypting it on the fly when you enter your user password.
Thus Prevent them from accessing your hard drive remotely without the password or that someone can access your information if your computer is stolen.
In search of malware
In case hackers obtain information through malware installed, it is advisable to track the contents of your computer both by accessing the installed applications in search of rare programs and with tools as classic but effective as an antivirus for macOS.
It is also worth reviewing the login elements to discover What processes start running once you turn on the computer. You can do it from ‘System preferences‘ > ‘General‘ > ‘Login Items‘.
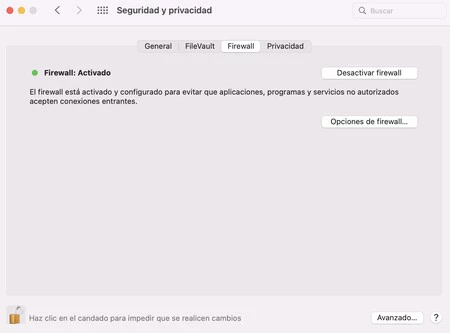
Activate and configure the Firewall
The firewall is a very effective tool to prevent hackers from taking advantage of vulnerabilities on your computer, acting as a a barrier that controls what enters and leaves your network data traffic. In this way, it protects you against unauthorized access and exploits remote.
Access the macOS Firewall from the ‘System preferences‘ > ‘Security and privacy‘and enter’Firewall‘. Once you activate it, you can enter the options to see which applications and services can request connections and block others.
Backups and factory resets
A general recommendation from technology specialists is that let’s make regular backups for times like these, since having a backup copy will allow us, in the event of an extreme emergency, to take the drastic measure of factory formatting our equipment without losing the most valuable information.
But there are people who continue to ignore the advice until it is too late. However, if you suspect that your Mac has been hacked and you have already disabled connections, you can still make a backup using the integrated Time Machine tool.
Afterwards it will only be format your Macin System Settings (‘System Preferences in macOS Monterey’) and in its homonymous menu click on ‘Delete content and settings‘. At this point, any third-party applications that have been installed (by you or hackers) will be deleted, which also includes malware. When it is finished and reinstalling, you should update to the latest version if supported before integrating your backup data.
Cover | Assembly with Smartmockups and Image by catalyststuff on Freepik
In Genbeta | How to back up your Mac before updating to the new version of macOS
[ad_2]
Source link








